LongRiverTech Consulting: A complete analysis of treasury fund management software

With the continuous development of technology, fund management plays an increasingly important role in corporate operations.
However, traditional fund management methods can no longer meet the efficient and accurate needs of modern enterprises.
Therefore, it is imperative for enterprises to introduce an excellent fund management software.
Today, I will give you a comprehensive analysis of all aspects of the treasury fund management software.
We will start with its definition and have a deep understanding of its core functions, characteristics and advantages.
In addition, we will also explore its application cases in enterprises, as well as the benefits and impacts it brings.
Through this introduction, I believe you will understand how to use this software to optimize the company's fund management process and improve the company's competitiveness and profitability.
Let us join hands in the new era of fund management and explore the opportunities and challenges brought to us by the treasury fund management software!

In this introduction, I will introduce the core content of fund account management to you through the following aspects.
First, we will explore in depth the importance of processing receipts and payments and its impact on enterprises.
Second, we will analyze the role and implementation methods of cash flow analysis to help enterprises rationally plan fund operations.
Then, we will introduce the principles and operation steps of the budget control function, and how to effectively use this function to achieve financial goals.
Next, we will explain the methods and key points of generating financial statements so that companies can understand their financial status in a timely manner and make corresponding decisions.
At the same time, we will also focus on the significance and establishment methods of audit tracking records to ensure the financial compliance of the company.
Finally, we will explore the importance of permissions and security, as well as the strategies and best practices for data backup and recovery to ensure the security and reliability of corporate capital accounts.
Let us study these key issues in depth and jointly improve the level of capital account management.

Capital account management is a vital part of the modern financial system. In terms of account opening and maintenance, we need to carefully select the right institution and follow relevant regulations. In terms of fund flow monitoring, real-time tracking of account dynamics is a key step to ensure fund security. In addition, multi-account coordinated management can optimize resource allocation efficiency and improve investment returns. Below I will introduce these important points in detail.
In this section, I will introduce the content of account opening and maintenance.
In the treasury fund management software, the account opening process is very convenient.
Users only need to follow the system prompts and fill in the relevant information to quickly open an account.
Next, I will introduce the account information maintenance method.
In the treasury fund management software, users can easily modify and maintain the opened account information to ensure the accuracy and timeliness of the account information.
Finally, I will focus on the account security strategy.
In order to ensure the security of user accounts, the treasury fund management software has multiple account security strategies, including password protection, login verification and other measures to effectively prevent illegal operations and information leakage.
Through these methods, we can better open and maintain accounts.
In this paragraph, I will use the theme of "fund flow monitoring" to elaborate on the functional characteristics of our treasury fund management software.
First, let's look at real-time fund flow monitoring.
The treasury fund management software provides real-time fund flow monitoring function, users can check the fund status of the account anytime and anywhere, and keep abreast of the inflow and outflow of funds.
This function can help users have a clear understanding of fund flow and make more informed decisions.
Secondly, let's take a look at the automatic alarm of abnormal transactions.
When an abnormal transaction occurs in an account, the treasury fund management software can automatically issue an alarm to help users discover and deal with possible risks in a timely manner and ensure the safety of funds.
This function can avoid losses caused by abnormal transactions and improve the security of funds.
Finally, let's take a look at the detailed flow record query.
The treasury fund management software provides a detailed flow record query function. Users can filter by time, amount and other conditions to facilitate in-depth analysis and audit of fund flow.
This function can help users conduct in-depth analysis and audit of fund flow, thereby improving the efficiency of fund use.
The above is the fund flow monitoring function of our treasury fund management software.
I hope this information can help you better understand and use our software.
In this section, I will share in depth on the theme of multi-account coordinated management.
In enterprise management, the existence of multiple fund accounts is a normal state, but how to effectively coordinate and manage these scattered fund accounts is a problem faced by many enterprises.
The emergence of the multi-account coordinated management module provides a solution for this.
First of all, through this module, enterprises can realize the aggregation of funds from multiple accounts.
This means that no matter which bank the fund account is opened in, it can be displayed on one platform.
In this way, enterprises can more conveniently carry out overall fund management and decision-making.
Secondly, this module also has the ability to monitor fund flow in real time.
Enterprises can clearly see the inflow and outflow of funds in each account, detect abnormal situations in time, and ensure the security of funds.
This is undoubtedly the key guarantee for the healthy operation of enterprise funds.
Furthermore, multi-account coordinated management also brings the function of optimizing fund allocation.
The system will automatically allocate funds reasonably according to the financial status and business needs of the enterprise.
This can not only improve the efficiency of fund use, but also avoid wrong decisions caused by human factors.
Then the content of this page is introduced here. Next, we will further understand the practical application and advantages of multi-account coordinated management.

In this paragraph, I will take the first-level outline payment and receipt processing as the theme, and introduce its importance and related second-level outlines.
First of all, payment and receipt processing is an indispensable part of enterprise operations.
It involves the company's fund flow, financial records and relationship with customers.
Below I will introduce three important points in detail: collection operation process, payment method setting and payment and receipt review.
The collection operation process is a key link to ensure that the company receives customer payments in a timely manner.
It includes a series of steps from customer ordering to payment receipt, such as invoice issuance, payment verification, and collection notice.
Through standardized operation processes, companies can reduce errors and delays and improve collection efficiency.
Payment method setting is a payment method strategy set to meet the needs of different customers.
Companies can choose appropriate payment methods based on customer preferences and payment habits, such as cash payment, bank transfer or electronic payment.
By providing a variety of payment methods, companies can improve customer satisfaction and promote sales growth.
Finally, there is the review of receipts and payments, which is an important link to ensure the accuracy of the company's finances.
After each transaction is completed, the company needs to check and confirm the receipts and payments.
This process includes reconciliation, voucher review, and internal control to ensure the accuracy and reliability of financial data.
In short, the processing of receipts and payments is crucial to the financial management and operation of the company.
By establishing standardized collection operation processes, flexible and diverse payment method settings, and strict review of receipts and payments, companies can effectively manage capital flow, ensure financial security and smooth business development.
In this section, I will elaborate on the collection operation process of the treasury fund management software.
First, the software supports multiple collection methods, including cash, check, bank transfer, etc., to meet the payment needs of various customers.
Secondly, once the payment is received, the software will automatically confirm and generate detailed collection records to ensure the accuracy and completeness of each payment.
Finally, for possible collection anomalies, such as inconsistent amounts or incorrect payer information, the software will immediately issue a reminder and provide a detailed exception handling process.
Through such an operation process, we can ensure that the collection work is efficient and accurate.
Next, let's take a closer look at the specific operation links.
In this section, I will discuss the payment method settings in the treasury fund management software.
In the treasury fund management software, we provide a variety of payment methods, including bank transfer, check payment, e-wallet, etc., to meet the payment needs of different users.
First, let's take a look at the payment method setting process.
Users can set and manage various payment methods in the software according to actual business needs.
For example, users can add new payment methods to meet specific business needs, or modify the parameters of existing payment methods to adapt to different payment scenarios.
In the process of setting up payment methods, security control is very important.
The treasury fund management software has strict security control mechanisms for each payment method to ensure the security of funds.
For example, we can verify the identity and authority of the user through the payment password, and we can also set up secondary confirmation to prevent misoperation or unauthorized transactions.
In short, the treasury fund management software provides flexible and diverse payment method options while focusing on payment security.
By setting and managing payment methods in the software, users can customize the configuration according to their own needs to ensure the smooth progress of the payment process.
In this section, I will take the key link of "Review of Payments and Receipts" as the theme, and introduce its importance and specific implementation steps in detail.
First of all, we need to understand the status and role of the audit process in fund management.
It is an important link to ensure the compliance and accuracy of each transaction and prevent the occurrence of financial risks.
An effective audit process is like a protective barrier, protecting the financial security of the enterprise and maintaining the financial health of the enterprise.
Therefore, we must attach great importance to and continuously improve this link.
Next, I will explain in detail how to set audit rules.
Audit rules are the core part of the audit process, which determines the efficiency and accuracy of the audit.
We need to set detailed audit rules, including amount limits, transaction types, etc., to make the audit process more standardized and efficient.
In this way, we can process a large number of transactions in a short time while ensuring the quality of the audit.
Finally, I will talk about how to deal with abnormal transactions.
For abnormal transactions found during the audit process, we need to conduct detailed investigations and handle them.
This can not only prevent possible financial risks, but also help us improve the efficiency and accuracy of the audit.
Therefore, for every problem found, we must not take it lightly, we must take it seriously, study it carefully, find out the root cause of the problem, and take effective measures to solve the problem.
In general, the audit of receipts and payments is an important and complex process.
We need to set strict audit rules, optimize the audit process, and promptly discover and handle abnormal transactions to ensure the safety and liquidity of corporate funds.

In this section, I will introduce cash flow analysis to you.
First, we will explore cash inflow analysis.
Cash inflow refers to the cash obtained by an enterprise in its daily operating activities through the sale of products, provision of services, or receipt of loans.
Next, we will discuss cash outflow analysis.
Cash outflow refers to the expenses incurred by a company to maintain daily operations, including purchasing raw materials, paying employee wages, and repaying debts.
Finally, we will calculate net cash flow, which is the company's cash inflow minus the net cash outflow in a certain period.
Through cash flow analysis, we can understand the profitability and cash liquidity of the company.
Below I will introduce the content of each section in detail.
In this section, I will analyze the sources of cash inflow in detail. Through in-depth data analysis, we can clearly grasp the company's main income channels, and then optimize resource allocation and increase profits.
Next, we will make trend forecasts for historical cash income, which will provide important reference for our company's future decision-making.
Finally, we will study the correlation between cash income and each business line to help us understand which businesses contribute most significantly to the company's earnings, so as to adjust the business strategy.
In this section, I will take the in-depth analysis of cash outflow as the theme to help everyone better understand and master the laws of cash flow.
First, we will explore the types of cash outflow.
Detailed classification of cash outflows, such as investment expenditures, operating costs, and debt repayments, will help us accurately grasp the direction and scale of funds.
Next, we will study the timing of cash outflows.
By analyzing the cash outflows at each time point, we can more clearly understand the payment rhythm and habits of the company, which is of great significance for us to optimize capital scheduling and management.
Furthermore, we will conduct an in-depth analysis of the proportion of cash outflows.
By comparing the proportions of various cash outflows, we can reveal the main financial pressures of the company, which will provide a strong basis for us to optimize the use of funds.
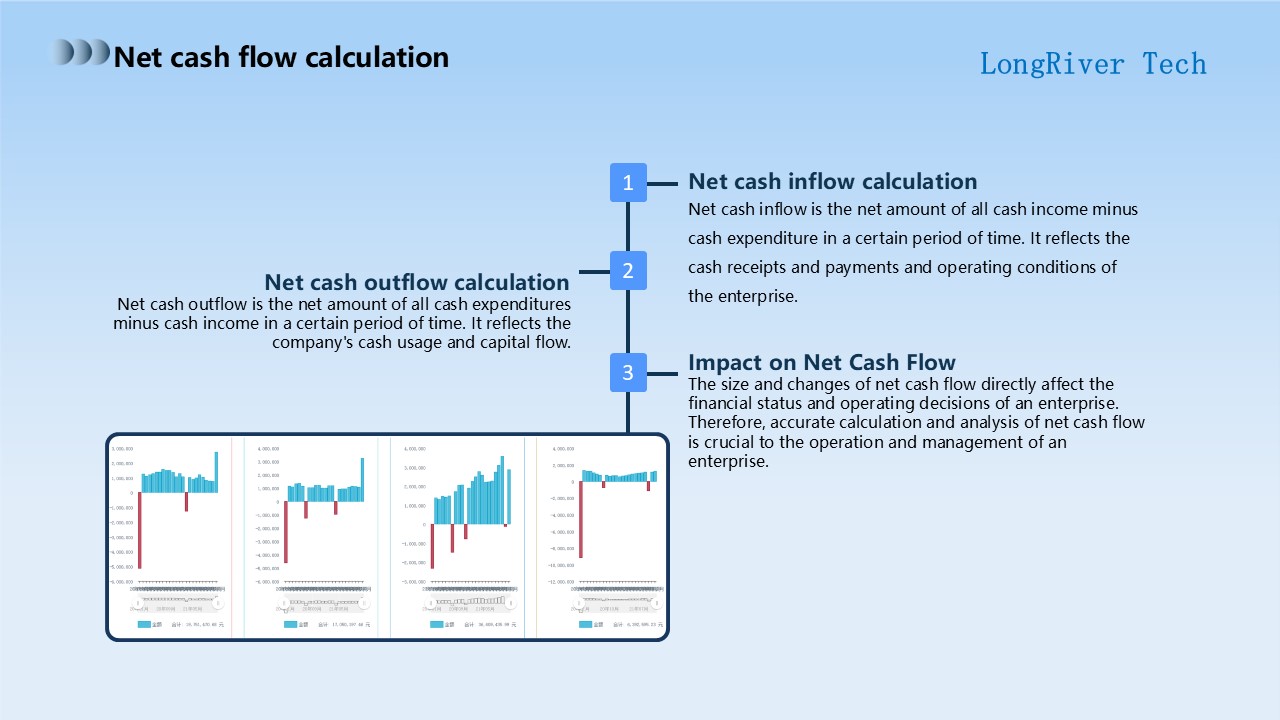
In this section, I will focus on the calculation of net cash flow.
First, let's discuss the calculation method of net cash inflow.
Net cash inflow is the difference between all cash income and cash expenditure of an enterprise in a specific period. It intuitively shows the cash inflow and outflow status and operating conditions of the enterprise, and has a vital impact on the assessment of the financial status of the enterprise.
Secondly, let's discuss the calculation method of net cash outflow.
Similarly, net cash outflow is the amount of all cash expenditures of an enterprise minus cash income over a period of time.
It reflects how the company uses funds and the flow of funds, and has important reference value for evaluating the efficiency and health of the company's funds.
Finally, we need to deeply understand the impact of net cash flow on the company.
The size and changes of net cash flow directly affect the company's financial situation and decision-making.
Therefore, accurately calculating and analyzing net cash flow has irreplaceable value for the company's business management.

The budget control function is a key component in corporate management.
First of all, we need to understand the importance of budget preparation and adjustment.
Budget preparation refers to the formulation of a reasonable budget plan based on the company's goals and needs, while budget adjustment is to make necessary revisions based on actual conditions.
Next, I will introduce the function of real-time budget monitoring.
By real-time monitoring of budget execution, deviations can be discovered in time and corresponding measures can be taken to ensure the effective implementation of the budget.
Finally, I will analyze the effect of budget execution.
By analyzing the results of budget execution, the effectiveness of the budget can be evaluated and improvement suggestions can be put forward to improve the economic benefits of the company.
In this section, I will take budget preparation and adjustment as the theme and explain in detail the key steps and strategies of budget management.
Budget preparation is an important part of treasury fund management, which mainly includes steps such as demand analysis, budget preparation, approval and execution.
In the budget preparation stage, we need to accurately predict and analyze the fund demand in order to provide sufficient financial support for the company's operation and development.
Next, we will discuss the budget adjustment strategy.
Budget adjustment is to adapt to changes in the operating environment and changes in internal demand. There needs to be a clear adjustment strategy and procedure to ensure the scientificity and effectiveness of the budget.
This includes regular evaluation of budget execution, timely identification of deviations, and necessary adjustments based on actual needs.
Only through flexible and effective budget adjustment strategies can we ensure that the company's use of funds is always in line with strategic goals and market needs.
Then on this page, I will focus on budget monitoring and feedback.
Budget monitoring is an important part of budget management. By real-time tracking and analysis of budget execution, it provides a basis for budget adjustment and provides feedback and evaluation on the budget execution effect.
Through an effective monitoring mechanism, we can promptly discover and solve problems in budget execution to avoid waste of resources and reduced efficiency.
Finally, I will briefly summarize the above.
Budget preparation and adjustment are an indispensable part of fund management and are of great significance to the operation and development of the company.
Through a rigorous budget preparation process, a scientific and reasonable adjustment strategy, and an effective monitoring and feedback mechanism, we can achieve the maximum value and optimal use of funds.
In this section, I will give a speech on the theme of "real-time budget monitoring".
As the scale of enterprises continues to expand and the economic environment becomes increasingly complex, effective budget management has become one of the keys to the success of enterprises.
As an important part of budget management, real-time budget monitoring provides enterprises with 24-hour uninterrupted tracking and analysis tools to help enterprises better grasp the budget execution.
Then on this page, we will explore the content of real-time budget monitoring in depth from three aspects:
Budget execution progress display, abnormal budget change alarm and its importance.
First of all, budget execution progress display is one of the important functions of real-time budget monitoring.
By using a graphical method, enterprises can clearly understand the progress of budget execution, including completed, unfinished and over-budget parts.
This not only facilitates the grasp of budget execution by senior management of enterprises, but also helps various business departments to make timely adjustments to ensure the reasonable implementation of the budget.
Secondly, the alarm for abnormal budget changes is another important function of real-time budget monitoring.
When there is an abnormal change in the budget, the system will automatically issue an alarm to help enterprises find and deal with problems in a timely manner.
This automated alarm mechanism effectively reduces the impact of human factors on the execution of enterprise budgets and improves the accuracy and efficiency of budget management.
In the last part, we want to emphasize the importance of real-time budget monitoring.
In today's rapidly changing market environment, enterprises need to keep abreast of budget execution in order to make accurate decisions based on actual data.
Real-time budget monitoring provides real-time data feedback and analysis, enabling enterprises to respond quickly to market changes and adjust business strategies to achieve better performance and competitive advantages.
The above is an overview of real-time budget monitoring, budget execution progress display, and the importance of abnormal budget change alarms.
As an important tool for modern enterprise management, real-time budget monitoring will help enterprises better achieve budget goals and improve operating efficiency.

In this section, I will focus on budget execution analysis and explore how to understand budget execution through real-time monitoring and data analysis.
First, we will focus on the analysis of budget execution progress.
Through continuous monitoring and in-depth analysis of data, we can grasp the actual implementation of the budget, including whether it is carried out according to plan and whether there are overspending or savings.
Next, we will focus on evaluating the effectiveness of budget execution.
Through comparative analysis of budget execution results, we can evaluate the effectiveness of budget execution, including whether the expected goals are achieved and whether there are deviations.
This evaluation will provide us with important feedback information so that we can adjust and optimize budget strategies in a timely manner.
In the process of budget execution, risks are inevitable.
Therefore, we will focus on the early warning of budget execution risks.
By predicting and warning of possible risks, we can timely discover potential problems and take corresponding measures to prevent major risks in the process of budget execution.
This will help to ensure the effective implementation of the budget and minimize possible losses.
In this page, we will explore in depth the three key aspects of budget execution: progress analysis, effect evaluation and risk warning.
Through these analytical methods, we will be able to understand the implementation of the budget more accurately and take corresponding measures in a timely manner to ensure the effective implementation of the budget.

Financial statement generation is a key financial management link.
Below I will briefly introduce the automatic generation of balance sheets, the display of income statements and profit and loss statements, and the analysis of cash flow statements.
First of all, the automatic generation of balance sheets is an important task.
The balance sheet is an important indicator of the financial status of an enterprise. It records the assets, liabilities and owner's equity of the enterprise at a specific point in time.
By using professional accounting software or tools such as Excel, we can quickly generate a balance sheet and ensure the accuracy and completeness of the data.
This will greatly improve the efficiency of financial work and provide timely and reliable basis for corporate decision-making.
Next, the income statement and profit and loss statement show information such as the income, cost, expenses and profit of the enterprise in a certain period of time.
These statements are essential for evaluating the operating status and profitability of the enterprise.
The income statement can clearly reflect the profitability of the enterprise, while the profit and loss statement takes into account all income and expense items more comprehensively.
By analyzing these financial statements in detail, we can gain an in-depth understanding of the operating status of the enterprise and provide important reference for formulating effective strategies and decisions.
Finally, cash flow statement analysis is an important tool for evaluating the cash flow status of the enterprise.
The cash flow statement records the inflow and outflow of cash in a certain period of time, including cash flow in operating activities, investment activities and financing activities.
By analyzing the cash flow statement, we can understand the source and use of funds of the enterprise, judge the debt repayment ability and operating stability of the enterprise, and make corresponding decisions for managing capital flow.
In short, financial statement generation is one of the basic tasks of financial management.
The automatic generation of balance sheets, the display of income statements and profit and loss statements, and the analysis of cash flow statements are all key steps for us to carry out effective financial management and decision-making.
By accurately and timely understanding the financial status and operating conditions of the enterprise, we can better grasp the development direction of the enterprise, optimize resource allocation, and achieve long-term and stable profit growth.
In this paragraph, I will focus on the automatic generation function of balance sheets in the treasury fund management software, and elaborate on its process, accuracy guarantee, and how to improve the efficiency of financial management.
First, let us understand the automatic report generation process.
In the treasury fund management software, the system can extract data from the database according to the preset parameters and algorithms, and organize and calculate it according to the format of the balance sheet.
Through this process, we can get accurate and consistent financial statements.
This automated process not only improves efficiency, but also reduces the possibility of human error.
Secondly, we have to talk about the accuracy of data.
In the process of automatically generating reports, the module will perform multiple data verification and verification.
This means that both the source data and the final results are accurate.
This is very important because it ensures that the financial information we get is reliable.
Then let's take a look at how to improve financial management efficiency on this page.
By using the automatic generation of balance sheets in the treasury fund management software, enterprises can greatly reduce the time and workload of manual operations.
This not only helps to improve work efficiency, but also ensures the accuracy and timeliness of reports.
This is a very valuable tool for enterprises of any size.
In summary, the treasury fund management software ensures the accuracy of data and improves work efficiency through the function of automatically generating balance sheets.
This is a powerful tool that is of great significance to the financial management of modern enterprises.
In this paragraph, I will focus on the display of income statement and profit and loss statement.
First, let's discuss the generation and interpretation of the income statement.
The income statement is an important part of a company's financial report. It shows in detail the company's revenue, cost and profit in a specific period, which helps the company understand its own operating conditions.
Through the analysis of the income statement, we can see the changing trends of key indicators such as the company's operating income and net profit, and then evaluate the company's profitability and operating stability.
Secondly, let's take a look at the composition and analysis of the income statement.
The income statement is an important report that reflects the results of a company's operating activities. It includes multiple indicators such as operating income, operating costs, and operating profit. Through the analysis of these indicators, the company's profitability and operating efficiency can be evaluated.
For example, we can compare the operating income share of different product lines and changes in cost structure to determine which products contribute the most to the company's profits and which products may need to be optimized.
Finally, we need to understand the generation and application of financial reports.
Financial reports include not only income statements and income statements, but also balance sheets, cash flow statements, etc., which together constitute the company's financial information system and provide important reference for corporate decision-making.
By comprehensively analyzing these financial statements, we can fully understand the company's financial situation, risks and opportunities, so as to make effective strategic and operational decisions.
In practical applications, the income statement and profit and loss statement can help investors, creditors and management make wise decisions.
Investors can evaluate a company's profitability and growth potential by analyzing these statements, and thus choose whether to invest.
Creditors can evaluate a company's debt repayment ability and risk level by analyzing these statements, and thus decide whether to provide loans.
Management can evaluate the company's operating conditions and performance by analyzing these statements, and thus formulate corresponding operating strategies and goals.
In short, the presentation of the income statement and profit and loss statement is crucial for us to understand the company's financial status and operating performance.
By in-depth analysis and comprehensive use of these statements, we can obtain valuable information and insights to provide strong support for the company's decision-making.
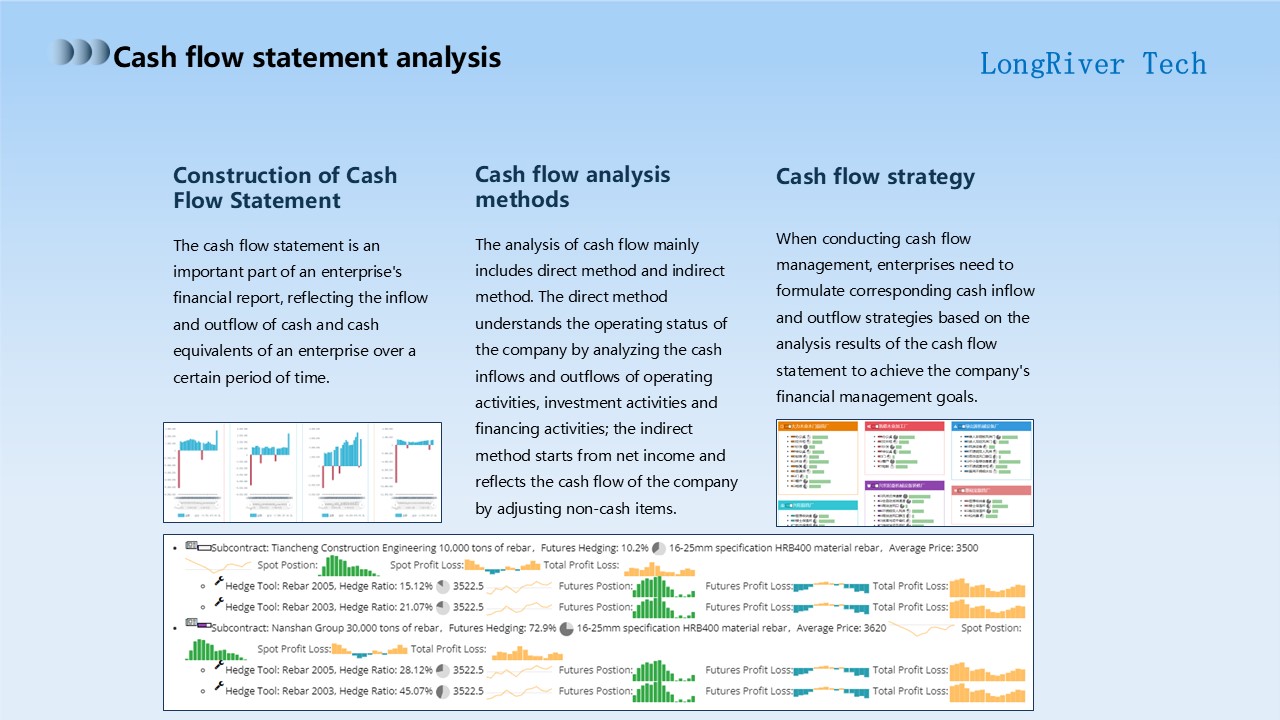
In this section, I will take the cash flow statement analysis as the theme and discuss the key aspects of this topic in detail.
First, let's focus on the construction of the cash flow statement.
As an important part of the company's financial report, the cash flow statement is centered on showing the inflow and outflow of cash and cash equivalents of the company in a specific period.
In this form, the company can clearly understand its cash management capabilities and make more informed economic decisions based on this.
Secondly, let's look at the cash flow analysis method.
There are two main methods for analyzing cash flow: direct method and indirect method.
The direct method can provide us with an in-depth understanding of the company's operating conditions by analyzing the cash inflows and outflows of operating activities, investment activities and financing activities.
However, this method requires us to have an in-depth understanding of each business in order to more accurately analyze the cash flow of each activity.
The indirect method starts from net income and reflects the company's cash flow by adjusting non-cash items.
Although this method is relatively simple, it may not fully reflect the company's actual cash flow.
Finally, we have to discuss the cash flow application strategy.
When managing cash flow, companies need to formulate corresponding cash inflow and outflow strategies based on the analysis results of the cash flow statement to achieve the company's financial management goals.
This requires companies to have good financial planning capabilities and sufficient flexibility to cope with changes in the market environment.
So on this page, we have conducted an in-depth discussion on the analysis of cash flow statements, including the construction of cash flow statements, analysis methods, and application strategies.

Audit tracking records are a key link in our comprehensive monitoring of corporate financial operations.
Among them, the fund flow monitoring function can grasp the flow of funds of the enterprise in real time and ensure the safety of funds.
At the same time, the automatic alarm function of abnormal transactions can detect and deal with possible financial risks in the first time to ensure the stable operation of the enterprise.

In this section, I will take the overview of audit trail records as the theme and introduce you to its definition, functions and importance in detail.
First, let's understand the definition of audit trail records.
As an important module in the treasury fund management software, the core goal of audit trail records is to record and track all financial transactions to ensure that the company's financial activities are legal, compliant, transparent and traceable.
This process not only includes detailed records of each transaction, but also continuous monitoring and analysis of these transactions in order to discover and correct possible problems.
Next, we will explore the functions of audit trail records.
The main functions of this tool can be divided into three aspects:
First, it can monitor all financial transactions in real time and provide the company with timely and accurate financial information;
Second, audit trail records can automatically generate various audit reports, thereby saving a lot of manpower and time resources;
Finally, it also provides transaction query and analysis tools to help companies improve the efficiency and quality of financial management.
So in this page, we have a basic understanding of audit trail records.
Next, I will introduce in depth the application and advantages of audit trail records in actual operations.
First, the importance of audit trail records is reflected in preventing financial fraud.
By keeping detailed records and continuous tracking of every transaction, we can promptly detect and deal with any suspicious or abnormal transaction behavior, thereby effectively preventing financial fraud.
Secondly, by monitoring all financial transactions in real time, audit trail records help ensure the accuracy of financial data.
Any errors or omissions may have a profound impact on the company's financial situation.
Therefore, audit trail records provide an effective mechanism to help us ensure the accuracy of financial data.
Thirdly, audit trail records can help companies meet the requirements of regulators.
Many countries and regions have strict regulatory requirements that require companies to keep detailed records and monitor all financial transactions.
By using audit trail records, we can ensure that companies can effectively conduct internal control and risk management while meeting these requirements.
Below I will further illustrate how to use audit trail records to solve some specific problems through a real case.
In this case, a company successfully discovered an internal theft involving a large amount of funds after using audit trail records.
Through the detailed transaction records and analysis tools provided by audit trail records, they were able to quickly locate the problem, take corresponding measures in time, and ultimately avoid greater losses.
In the last part, we will further explore how to optimize and improve our audit trail record system.
Whether from a technical or management perspective, there are many ways to help us use audit trails more effectively and improve the efficiency and quality of our financial management.
In general, audit trails are an important tool that can help us better manage our finances, prevent risks, and meet regulatory requirements.
In future work, we need to continue to learn and master this tool and use it to its full potential.

In this section, I will use the funds flow monitoring function as a starting point to explore how it can help companies manage their funds.
First of all, the real-time funds flow monitoring function is the core of this function.
It can track and record the company's funds inflow and outflow in real time, helping treasurers understand the company's financial situation.
Through this function, treasurers can grasp and manage the company's funds flow in real time, so as to make more accurate decisions.
Secondly, the abnormal funds change alarm mechanism of this function is also a major feature.
When the company's funds flow is abnormal, the system will automatically issue an alarm to help treasurers find and deal with possible problems in a timely manner.
This is crucial to prevent financial risks and ensure the company's financial security.
Finally, by analyzing the cash flow data, it can help the treasurer understand the company's financial situation and provide a basis for decision-making.
The existence of this function has transformed the fund management from the previous "experience-driven" to "data-driven", greatly improving the accuracy and efficiency of decision-making.
So on this page, we have explained the main functions and roles of the fund flow monitoring function. Next, we will move on to the next topic.

In this paragraph, I will introduce our abnormal transaction monitoring system with the theme of "Automatic alarm for abnormal transactions".
The system first has an automatic abnormal transaction identification module, which can monitor and analyze the flow of funds in real time. Once abnormal transaction behavior is found, the system will immediately mark and alarm.
In this way, we can quickly locate and deal with abnormal situations to avoid losses caused by time delays.
In addition, our system can also intelligently classify abnormal transaction types according to preset rules.
These abnormal transactions include but are not limited to large transactions, frequent transactions, and continuous transactions in a short period of time.
With such classification, we can more accurately understand which types of abnormal transactions pose a threat to our business, so as to adopt targeted strategies to deal with them.
Once an abnormal transaction is detected, our system will automatically send an alarm message to the relevant personnel and start the preset processing process.
This can ensure the safety of our company's funds and reduce the risks caused by untimely or inaccurate processing.
On this page, we introduced the application of the automatic abnormal transaction identification module, the classification of abnormal transaction types, and the abnormal alarm processing process.
This powerful system will play an important role in our daily operations and ensure the safety of the company's assets.

In the field of information security, permissions and security are crucial.
First, let's talk about user permission settings.
Effective user permission settings can ensure that information can only be accessed by authorized users.
Secondly, data security is our core responsibility, including data encryption, backup and recovery measures.
Finally, audit and log tracking can help us monitor and analyze system activities, detect abnormalities in time and take corresponding measures.
I will introduce these in detail below.
In this section, I will introduce the user permission settings in the treasury fund management software, and elaborate on how we define different user roles, adopt flexible permission allocation strategies, and establish permission adjustment and audit mechanisms to ensure the normal operation of the system and the integrity of data.
So on this page, we first want to explain the user role definition.
In the treasury fund management software, in order to achieve efficient operation, we set up a variety of user roles according to different job responsibilities and task requirements, such as administrators, operators, etc.
The existence of these roles not only meets various work needs, but also ensures the improvement of system functions and stable operation.
Next, we will discuss the permission allocation strategy.
We have adopted a flexible permission allocation strategy, that is, according to the user's role and responsibilities, give corresponding data viewing, modification and deletion permissions.
This can ensure both data security and data accuracy.
Each permission allocation is based on actual business needs and user role responsibilities, aiming to create a safe and effective working environment for each user.
Finally, we want to emphasize the permission adjustment and audit mechanism.
In order to ensure the normal operation of the system and the integrity of data, we have established a permission adjustment and audit mechanism in the system.
Regularly check and adjust user permissions, and record all operation logs for auditing.
This mechanism can not only prevent problems caused by excessive or insufficient permissions, but also promptly discover and correct any possible security risks.
The above is our introduction to user permission settings.
I hope that through our sharing, everyone can have a deeper understanding of user permission settings in the treasury fund management software.
Then on this page, I will introduce our data security measures to everyone.
First, we use advanced data encryption technology in the process of data transmission and storage.
Through this technology, all sensitive information can be protected from any unauthorized access and tampering.
Secondly, we strictly manage user permissions.
Each user's access rights are strictly controlled and allocated, and only authorized users can access the corresponding data and functions.
Such a design effectively prevents internal and external data leakage risks.
Thirdly, our treasury fund management software has security auditing and monitoring functions.
This function can record and analyze all operation behaviors in real time, and promptly discover and handle any abnormal situations.
The purpose of this is to ensure the stability and security of system operation.
The above are our data security measures.
We are well aware of the importance of data, so we have adopted these measures to ensure the integrity, availability and confidentiality of data.
In this section, I will explore the theme of audit and log tracking, and introduce the audit record function, log tracking system, and permission and security settings of the treasury fund management software in detail.
First, let's take a look at the audit record function. The audit record function of the treasury fund management software can record all operation processes in detail, which is convenient for later review and analysis.
The importance of this function is self-evident. It ensures that every capital flow is traceable and provides a solid foundation for capital management.
Next is the log tracking system.
The log tracking system can track and record all operation behaviors in real time, thereby providing strong protection for capital security.
Through this system, we can timely understand the use of funds, discover abnormal behaviors and take corresponding measures.
This real-time monitoring is crucial to ensure the security of funds.
Finally, let's take a look at the permission and security settings.
In the treasury fund management software, the permission and security setting function can clearly define the operation permissions of each user to prevent unauthorized personnel from performing illegal operations.
Through reasonable authority allocation, we can ensure the security of funds and reduce potential risks.
In summary, the audit record function, log tracking system, and authority and security setting functions of the treasury fund management software together constitute a powerful fund management system.
The introduction and use of these functions provide all-round protection for the management and security of funds.

Data backup and recovery are important topics for our discussion. First, let's look at the overview of data backup strategies.
In the digital age, data backup is particularly important, which can prevent data loss or damage.
Next, we will learn how to set up automatic backup settings and improve backup efficiency through automation.
Finally, we will explain the data recovery process in detail so that data can be quickly restored in the event of an accident.
In this section, I will discuss the importance of data backup strategy.
Data backup is a key measure to prevent data loss, especially for enterprises. Once data is lost, it may not only lead to significant economic costs, but also cause a credibility crisis.
Therefore, it is crucial to choose a suitable data backup strategy.
When choosing a data backup strategy, multiple factors need to be considered.
First of all, the importance of data. For key business data and sensitive customer information, a higher level of backup protection measures need to be taken.
Secondly, the backup cycle. According to the frequency of data changes and the speed of update, you can choose to back up data daily, weekly or monthly.
In addition, you should also choose the appropriate backup method according to different data types and scales, including local backup, cloud backup and off-site backup.
After data loss, how to recover data is also a key technical challenge.
Data recovery is to restore the original data by using the backed-up data, which requires professional technology and tool support.
By regularly testing and maintaining the integrity and availability of backups, the success rate of data recovery can be increased and possible risks and impacts can be reduced.
In summary, the choice of data backup strategy is of great significance to the operation and risk management of enterprises.
Through reasonable backup plans and effective recovery methods, enterprises can reduce the losses and risks caused by data loss and ensure the continuity and reliability of business.
In this section, I will introduce how to set automatic backup to ensure the security of financial data.
First, users can set specific backup times, such as daily, weekly or monthly, through the automatic backup function to ensure timely backup and recovery of data.
Secondly, when selecting the backup file type, users can select the file type to be backed up according to their needs, such as database files, log files, etc., to meet different backup needs.
Finally, users can set the storage path of the backup file, which can be a local hard disk or a network drive to ensure the security and easy search of the backup file.
In this section, I will focus on the process, steps and precautions of data recovery, and elaborate on this important link in detail.
First, let us understand the importance of data recovery.
Data recovery plays a vital role in fund management software. It can retrieve lost or accidentally deleted data from backups to ensure that our financial information is safe and intact.
This is like our safe. Even if it is locked due to forgetfulness or erroneous operation, we have the ability to open it in the right way and retrieve our precious assets.
Therefore, data recovery has a vital impact on our work.
So, what are the specific steps of data recovery?
First, we need to select a recovery mode.
Different modes are suitable for different scenarios, so choosing the right recovery mode is the key to success.
Next, we need to scan for lost data.
This step is like looking for our lost books in a huge library. We need to use professional tools for precise scanning and positioning.
Then preview and confirm the recovery content. This is to avoid recovering irrelevant or erroneous data and ensure that we only retrieve the information we really need.
The last step is to perform the recovery operation, which is the last step for us to retrieve the data. It needs to be done carefully and precisely.
There are some key considerations that we need to follow when performing data recovery.
First, we need to avoid large-scale write operations after the original data is lost, because this may overwrite the data we are trying to recover.
Secondly, regular data backup is also an effective means to prevent data loss.
Just as we will not find the door locked after losing the key, prevention is always more effective than solving the problem.
In this introduction, we have analyzed in detail all aspects of treasury fund management software.
From fund account management to payment processing, to cash flow analysis, budget control functions, financial report generation, audit tracking records, permissions and security, and data backup and recovery.
Through the introduction of these contents, we have a deep understanding of the importance and application value of fund management software. Thank you for listening.